A lack of . . . integrity?
A trip back to the 70's to look at the origin of modern security thinking.
The next time someone wheels out the CIA Triad or puts a risk grid in front of your face, you should shoot them a narrow look, the same look as if your GP had put a box of leeches on the desk with the intention to treat an illness. There are many who hold the CIA triad to be a foundational concept in security (It’s not). We have read many times that the CIA triad stands for Confidentiality, Integrity, and Availability. It has been around for nearly half a century. A NIST Special Publication from 1977 gives the following definition
It turns out that it’s not just CIA that has been around for half a century. It’s way worse than that.
SP 500-19 - Retro Security
SP 500-19, Audit and Evaluation of Computer Security | CSRC (nist.gov)
The NIST paper SP 500-19 is possibly one of the first instances where the terms confidentiality, integrity, and availability appear together in the context of security. The paper is a summary of an invitational workshop on the “Audit and Evaluation of Computer Security”. There were a range of subjects over ten sessions which provided recommendations for future development in the practice. It essentially outlines the foundation of what security practice has become, or at least how the mainstream conceptualise security. It discusses system acquisition, development security, operational security, logging, monitoring. It talks about policy from the top informing processes and practices. It talks about asset inventories, access control lists, separation of duties, configuration management, back up, recovery, and all sorts of other areas that don’t feel out of place today. They don’t feel out of place because how the industry talks about these things hasn’t changed. The paper discusses privacy in some detail which is perplexing as security practitioners didn’t seem to think this existed in a security conversation prior to GDPR.
There were some obvious pre-cursors to this. Confidentiality was introduced as a concept related to security in 1976 by Bell & La Padula. You will be familiar with those names if you have read any revision of a certain CBK. We need to keep in mind that this was from a time before the internet was available and even before the release of Doom. Computer systems were far from ubiquitous within organisations. The report itself is typed, betraying its age.
The contributors to this report were clever people and there are some really insightful parts to this special publication. They had made attempts to put some thought into the problem at a time where existing thinking was scant. They had even anticipated some problems in understanding security and touched on the problem with security frameworks, and it seems like their diagnosis is still valid.
But there is rough with the smooth and unfortunately most of the content has little to no application in a modern context.
Retro Risk
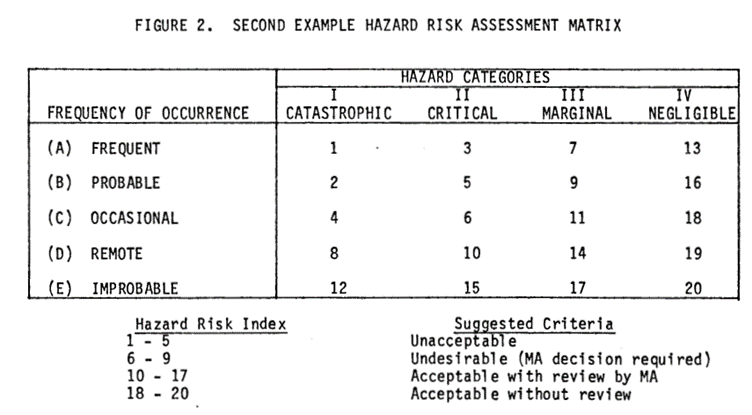
Another interesting quirk is that the paper goes on to discuss risk analysis and threat assessment. This gives us the probability, and impact.
A DOD standard also from 1977 gives us a risk assessment matrix. When combined with probability and impact are the basis of risk assessment as it exists today.
882b1.pdf (mit.edu) & MIL-STD-882B.pdf (ymaws.com)
The modern definition of ‘risk’ is a little bit of an issue. NIST publish at least 29 separate definitions for ‘risk’ but at their core they contain generally say something about the ‘probability or likelihood of harm caused by a future event’. How we think about risk also hasn’t changed in half a century.
The paper even talks about “unacceptable levels of risk”, essentially a proto “risk appetite”. Appetite is something like ‘want’ or ‘desire’. Is the declaration of a risk appetite statement of intent for masochistic tendencies, or perhaps sadistic ones? Maybe that depends on where the consequences of that risk land. Can you say that a sadomasochist characterisation of risk practitioners is inconsistent with your experience? The whole “risk” thing seems like it’s become an unintended consequence bereft of nuance.
The Cult of the Triad
So how come nothing has changed? The authors of the NIST publication stated quite explicitly that this was to identify areas to research further yet it doesn’t feel this happened in any meaningful way.
Consider for a moment how we pride ourselves on our ability to scrutinise, to analyse, to discern. Yet we do not apply the same scrutiny to our own foundations. To do so raises eyebrows. We have deified these ideas and embedded them within our texts. To remove it would undermine our certifications, our frameworks, and our models of Security. It is for this reason we cling to it like a lost child clinging to a comforting toy. Without it, everything falls.
Many of us deal with cutting edge technology and with no sense of irony choose to view this through a lens of dated thinking, deluding ourselves into believing what we are doing is security where at best it’s compliance. We hold to the belief that this is providing us with structure, with order, with credibility. But it has become a self-imposed limitation to dull our minds.
Some have tried to update the model, by adding different elements. But smashing a cornetto into the face of a horse does not create a unicorn. It is still a horse and what comes out of it is still shit. Gartner tried adding safety, NIST once alluded to the addition of safety and privacy. And there was the one who borrowed from the CIA triad of cryptography, added authenticity, followed by control and utility. All these are now consigned away to a footnote and are the apocryphal of our texts, only available to those who seek it.
There was another who introduced the DIE triad, distributed, immutable, and ephemeral. This was supposed to replace the CIA triad but moves us further away from the purpose of security and flirts dangerously close to the marketing literature for containerised solutions. He tried his hardest to send us into the desert of IT bullshit for forty years.
The efforts of those that tried to change this so show us something though. It shows what we already know, it’s incomplete at best, incorrect at worst. But if either is true, sweeping areas of Security orthodoxy must be discarded. Would correction be an admission of failure? An admission that what has been built has been done so without due care. As an industry, we are asleep at the wheel.
There are many reasons why the CIA triad and many of the related concepts in this NIST paper never served us. It frames our conversations in a way that puts us at odds with those we are trying to protect. It’s limited to talking about a subset of concerns, it anchors us to a world view of system, data, and infrastructure. We talk in terms of the pillars of security, or the objectives of security preventing disclosure, alteration, or denial which consigns protection or response to an ancillary concern.
There are technical issues with applying this thinking to modern solutions. How far would you extend availability and develop auto scaling system when you are on the meter in a public cloud? Could your technical defences become the very thing you are attacked with? What does ‘integrity’ look like in AI systems that perform black box operations by design? And knowing all this, how do you prioritise ‘vulnerabilities’ in good conscience knowing that at its core, CVSS is predicated on CIA.
The institutions upheld the idea, preaching the good word, but it was not good. Myopic in scope and bereft in creativity they lined their pockets with the ideas of the dead. They should know better as they represent us to business, to government, and to anyone who will listen. By embracing such concepts, they have turned our house into a den of thieves.
This all betrays something about modern security practice, it’s not really modern. And is this where it all went wrong.
Revelation
As practitioners, we are not blameless. We have debauched ourselves with easy answers to complicated questions. But we are an industry of people seeking quick answers, free templates, easy to follow standards. The construct of our industry doesn’t require more than our unwavering conformance to lists of things to be checked off. The bar is low.
It is with these ideas we have indoctrinated ourselves and become intoxicated with our own self-importance yet show ourselves to be mostly impotent and ineffectual. It is time to operate somewhere different, looking at the processes the systems support, and the strategy the processes support. If security is a problem of human behaviour as everyone says, why have we oriented ourselves around technological considerations?
Consider what we are here to do. Then consider what our current orthodoxy address and what it does not. Also consider where this came from and how it hasn’t changed.
Do you see the problem yet? Or will you persist with a failure of integrity?